
Master in Cybersecurity
- ONLINE
- 60 ECTS
- 7500€
- OPEN CALL
- 12 MONTHS
- SPANISH
The Master in Cybersecurity provides professionals and managers with the necessary strategies, knowledge and tools to work on data security, focusing on guaranteeing continuity in operations and permanence in the markets. This programme has been recognised in the TOP 2 in Spanish in the Cybersecurity, Systems Security and Data Protection category of Eduniversal's Best Masters Ranking.

Master in Cybersecurity (Spanish)

Universitat de Barcelona
Get a double degree from our academic partner, the reference university in Catalonia and Spain with more than 560 years of history behind it.

QS Stars Rating System
We are the first 100% online Business School in the world to receive the QS Stars rating, obtaining the highest distinction, five QS Stars, in the Online Learning category.

ISACA's certification
This Master prepares you for the CISA (Certified Information System Auditor) certification awarded by ISACA (Information Systems Audit and Control Association).
Syllabus for the Master's Degree in Cybersecurity
Our programme is structured in 3 blocks and culminates with the Master's Thesis. In addition, during the development of the programme, students will be able to enjoy 3 voluntary bootcamps and different additional activities.
Block 1. Initiation
Block 2. Deepening
Block 3. Overview
Master's Final Proect
Bootcamps and Additional Activities
1. Initiation
A first approach to the whole area of cybersecurity within organisations will be fundamental for a better understanding of all its components. In this module, students will learn about different elements and key concepts of cybersecurity, the different types of attacks and the Deep Web, among others.
Professor: Óscar Quero Hijano, Tech & Supply Manager at EAE Business School Madrid.
VIEW LINKEDIN
In order to properly manage cybersecurity in a company, it’s important to know about the different options available and the areas in which each solution can be applied. In addition, it is necessary to know everything that must be done in the company to be prepared for conflictive situations. Throughout this course, students will delve into topics such as the security plan, risk management, ISMS and the national security scheme, among others.
Professor: Noelia Valverde Pérez, Head of the Operations Department at Agroseguro.
VIEW LINKEDIN
2. Deepening
Cybersecurity doesn't rely on a single IT element within the company; it extends across the entire technological platform. The security vision must be comprehensive, covering different information systems, their databases, and operating systems. This module helps understand the scope of Security Management within the company, managing users, technologies, accesses, controls, etc.—everything that impacts security.
Professor: Miguel Agüero González, Head of IT Audit at Empresa Nacional de Telecomunicaciones - Entel S.A.
VIEW LINKEDIN
Companies are increasingly implementing more services in the Cloud, making it important to have a clear and efficient strategy to ensure the security of everything implemented, which also involves Cloud providers. In this subject, students will learn about the Cloud and its risks, identity access, proactively detecting vulnerabilities, Cloud providers, and agreements.
Professor: Ricard González Tejero, Director of DATA & AI Business en Conecta Wireless.
VIEW LINKEDIN
Ethical Hacking is key to find out if our systems have security issues, so it's essential to understand what it consists of, how it's done, and the tools commonly used to carry it out. Some topics you'll delve into in this module are penetration testing, pentesting, the phases of ethical hacking, and tools for Ethical Hacking.
Professor: Alejandro Hernández Martín, Perimeter Security Auditor and Ethical Hacker at Alten.
Analysing security events is a key aspect in maintaining optimal security levels in companies. This module covers all aspects related to forensic analysis, from methodologies to execution, including how expert opinions are conducted.
Professor: Ángel Escudero Molina, Security & GRC Advisor at GOVERTIS Advisory Services S.L.
VIEW LINKEDIN
Cryptography's main purpose is to encrypt messages containing sensitive data for the organization and its clients. Many operational business processes require protection and cannot be viewed under any circumstances by external elements, such as bank transfers, e-commerce, etc. This module reviews some of the main technological solutions used to maintain information encryption and will help students understand the nature of these solutions, their scope, and impact on implementation, as well as its subsequent management.
Professor: José Alberto Gordo Bravo, Cryptography - Security Architecture at BBVA.
VIEW LINKEDIN
3. Overview
The intensive use of information and communication technologies for managing business-supporting information exposes information assets to cybersecurity risks that are essential for business activities and the provision of public services. Protecting these assets has become a matter that extends beyond organizational decisions; it has evolved into a set of legal obligations that must be adequately addressed. This module reviews the main legal requirements and consequences to consider when making decisions about Information Security.
Professor: Ramón Miralles López, Cyber Law Specialist Lawyer at Ecix Group.
VIEW LINKEDIN
This subject will provide you with a general overview of the security tools available in the market. Beyond just knowing the tools themselves, it enables the identification of their main features and indicators to consider in the selection process. This subject will help students understand all the elements to be considered for the evaluation and acquisition of a technological solution.
Professor: Ángel Gálvez, Global CISO at DUFRY.
VIEW LINKEDIN
The auditing of computer systems and information technology governance processes is especially relevant to ensure the achievement of organizational objectives. The ongoing automation of business processes generates a reliance on the efficiency of computerized processes, which makes computer failure a business risk to keep in mind. Reviewing the existence and efficiency of management and computer security controls is an essential obligation for organizations. Throughout this module, students will delve into topics such as internal and perimeter security, web auditing or computer forensics, among others.
Professor: Albert Martínez Aparisi, CIO at Francesc de Borja Hospital.
VIEW LINKEDIN
Master's Final Project and Additional Activities
This program is designed to complement the thematic block content with the necessary training. The training is conceived from a threefold perspective: technical assistance, personal support, and the presentation of individual and group challenges necessary to achieve the set objectives.
Levelling Course | Fundamentals for Cybersecurity
OBS Business School provides students with a levelling course that allows them to acquire the necessary knowledge and skills to properly follow the program. This workshop is self-directed and voluntary. However, it is highly recommended for students from non-technical engineering backgrounds. Through the development of this course, students can identify areas they need to reinforce.
Complementary education
Prior to the start of the programme, students will be given access to different resources in order to acquire the necessary knowledge and develop the required skills for proper course follow-up. These courses will be guided by an instructor until the effective start of the program, and said supplements include:
- Introduction to Programming: Python
- IT Infrastructure
- Mathematics and statistics
Pre-Masters Bootcamps
The student will have the opportunity to take 3 Pre-Master Bootcamps that will be opened progressively and can be taken at any time. Once the course has been completed and passed, a certificate of completion will be awarded to the student.
- Bootcamp 1. Personal Branding
- Bootcamp 2. Data Storytelling
- Bootcamp 3. Creative thinking and innovation
- Bootcamp 4. Generative AI: Prompt Engineering
In addition, students will also have the opportunity to take these pre-master courses; however, these are available in English only:
- Building Your Professional Brand for Employability and Career Success
- Finance Fundamentals
- Organizational Well-Being
Introductory workshop | Campus Training
Before the start of the academic year, students will have the opportunity to attend an introductory workshop on the Campus, where they will be provided with the necessary tools and knowledge for the correct use of the platform during the academic year.
Professional Development Programme (PDP)
Two weeks before the start of the academic year, students will be able to participate in a professional development programme, where they will work hand in hand with a teacher to develop skills such as time management, productivity, stress management and emotional intelligence. Once the student has successfully completed the workshop, he or she will receive a certificate of completion.
The Master's Thesis is a fundamental element in the development of the Lifelong learning Master's degree in Cybersecurity. Throughout the process, students must consider all elements related to the development and management of a technology project based on IT security. The work is primarily framed based on its scope, duration, cost, and risks—factors that will be addressed following the current best methodological practices in Project Management.
Professor: Óscar Quero Hijano, Tech & Supply Manager at EAE Business School Madrid.
VIEW LINKEDIN
The Master's program in Cybersecurity is complemented by conferences and seminars held in each of the blocks. These additional activities are conducted by recognized professionals in business management who share their experiences and practical cases through video conferences.
Levelling Bootcamp: Fundamentals for Cybersecurity
A voluntary and self-directed course that OBS offers to students to reinforce their knowledge and skills in order to adequately follow the program.
Ethical Hacking Bootcamp
In this subsequent bootcamp, you will apply the knowledge acquired during the Ethical Hacking module through the development of practical cases.
Professor: Alejandro Hernández Martín, Perimeter Security Auditor and Ethical Hacker at Alten.
IT Project Management Bootcamp
The leaders responsible for maintaining Information Security in the Company will be thoroughly familiar with project management methodologies and best practices. As the company improves day by day, adapting its strategy and generating new information and security requirements, these changes will demand initiatives that translate into "Projects". Therefore, understanding project management, recognizing the organization's culture and knowing the models and best practices that might be more suitable in a cybersecurity project are essential.
Professor: Óscar Quero Hijano, Tech & Supply Manager at EAE Business School Madrid.
VIEW LINKEDIN
CISM Certification Bootcamp (Certified Information Security Management)
CISM is one of the most internationally renowned certifications in Information Security. It is granted by ISACA (Information Systems Audit and Control Association) and accredited by ANSI (The American National Standards Institute). This programme offers an optional specialized bootcamp to prepare students for the certification exam.
Professor: Albert Martínez Aparisi, CIO at Francesc de Borja Hospital.Ç
VIEW LINKEDIN
Company visits
During the development of the programme, the student will have the opportunity to attend synchronous videoconferences with professional experts that will share their experience and provide advice on some of the best practices in the sector.
Webinars
Most of the training is done asynchronously, that is, the exchange of knowledge is done through a platform that allows sharing written texts without the need for people to be connected at the same time. Additionally, in each of the modules, synchronous sessions or 'webinars' are organised, where all participants are connected at the same time through an application, which allows the exchange of knowledge in 'real time'.
Students taking the Lifelong learning Master’s degree in Cybersecurity will have the opportunity to prepare for the following certifications:
- ISACA’s CISM Certification
- ICN Business IT Certification
• Certificación Scrum Master & Product Owner
• Certificación Scrum Master@Scale
• Certificación Productot Owner@ Scale
• Certificación Value Stream Management
*The cost of the certifications, as well as the preparatory course, is not included in the price of the programme.
Methodology

OBS has an online methodology where the core is the student. Always backed by active and internationally renowned lecturers, who share their knowledge to enhance the professional development of students through a flexible, collaborative method with personalised monitoring. The aim is to create a unique educational experience that allows the assimilation of knowledge in a practical way.
Student ON's fundamental pillar is the student and, for this reason, throughout the course students have their Programme Manager, an academic figure who accompanies them in a personalised way.
Diploma
After successfully finishing the Master's degree, and having completed the relevant procedures, you will receive the Master's degree from OBS Business School. In addition, and provided that you meet the established academic and administrative requirements, you will obtain a Lifelong learning Master's degree from the Universitat de Barcelona (UB).
In order to obtain it, you must have a university degree. In the exceptional case of not having this degree and having passed the Master's evaluations, you will obtain a Higher University Diploma from the Universitat de Barcelona (UB).
At OBS Business School we are committed to having our own degree, which allows us to quickly update and adapt the programmes in each edition to be at the forefront of the educational level demanded by companies today. Our programmes are designed for professionals who want to strenghten their management skills and learn through an international experience.

Admission Process
The fundamental aim of our admissions process is to ensure the suitability of candidates. All participants should get the most out of this learning experience, through a context in which it is possible to develop long-term relationships with classmates, faculty and alumni.
After completing the application form for one of our programmes, you will receive an e-mail with information about the School and a member of the Admissions Department will contact you to start the admission process.
Once you have successfully passed the personal interview, you must submit all the required documentation to continue the admission process and certify that you meet the requirements of the student profile. After the Admissions Committee, if it is positive, you will be able to register and enrol in the programme you have applied for.
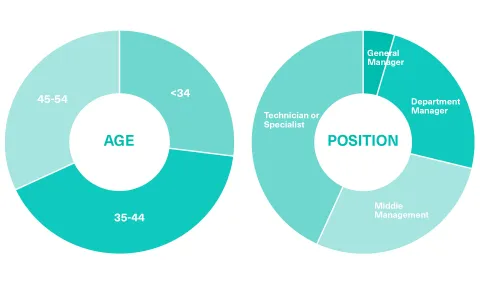
Student Profile
The students in the Lifelong learning Master’s degree in Cybersecurity come from diverse backgrounds and sectors, however, they all share a common goal: enhancing their managerial skills to propel their professional careers.
Professional Opportunities of the Master in Cybersecurity
This Master’s degree will help you boost your professional career as:
- Systems Auditor
- IT Specialists
- Network Administrator
- Database Administrator
- IT Security Consultant
- Security Officer
- Cybersecurity Analyst
- IT Risk Manager
- Systems Developer
- Infrastructure Administrator
- IT Security Project Manager


